Vulnhub Pluck 1 Walk Through
This article is walk through for Pluck1 boot2root machine.
Can be download from vulnhub:
https://www.vulnhub.com/entry/pluck-1,178/
As a shortcut, exploit knowledge I use in this machine:
LFI
Shell escape
SUID exploit
Let's start
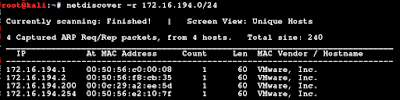
First as always, find the address by netdiscover or arp-scan
-r is for 'range' option
Information Gathering
After found address, use nmap to scan which port is open, we got 22, 80, 3306
First start with http, we see a page and with some option on the top
When I browse the About option, it shows some file with URL page=about.php
It means it could be LFI if it don't have sanitize input
So next I try to put page=../../../../../etc/passwd
Bingo!
Got passwd file and on the bottom line there is an interesting user name backup with a script file
Use LFI again to see what's inside this file
content is
we can get in via tftp and in file /backup.tar, it zip /home and /var/www/html folder's file
So we need to find out this file by accessing with tftp and download the file
After download, in /home/paul/keys/ there are several id_key files
So what's mean here, it is ssh key, we can use the key file to access machine without password
And id_key4 works, command is ssh -i id_key4 paul@172.16.194.200
After getin, instead of a terminal, we see a limited function here:
This is not good for our further exploit, so we need to escape this shell
Here there are two ways to escape, one is through Edit file (vi)
https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells
Another one, lynx shell escape can be found here:
http://insecure.org/sploits/lynx.download.html
enter the following in WWW option
LYNXDOWNLOAD://Method=-1/File=/dev/null;/bin/sh;/SugFile=/
So we have normal shell here!
Before we start Privilege Escalation, is always a good idea to make sure we have fully functional shell, there are many options
bash works in this case
Now we have a functional shell for we to do next step!
Privilege Escalation
After some trial, I found a SUID bit set program:
exploit URL:
https://www.exploit-db.com/exploits/39535/
I know it's wired to say even though version is not match but it still works.....
This is the script file, store on /tmp, which is world writable,
and remember the permission need to set to 777
Exploit, and finally become root :)
Thanks for watching!!
-Billy














留言
張貼留言