Vulnhub Stapler1

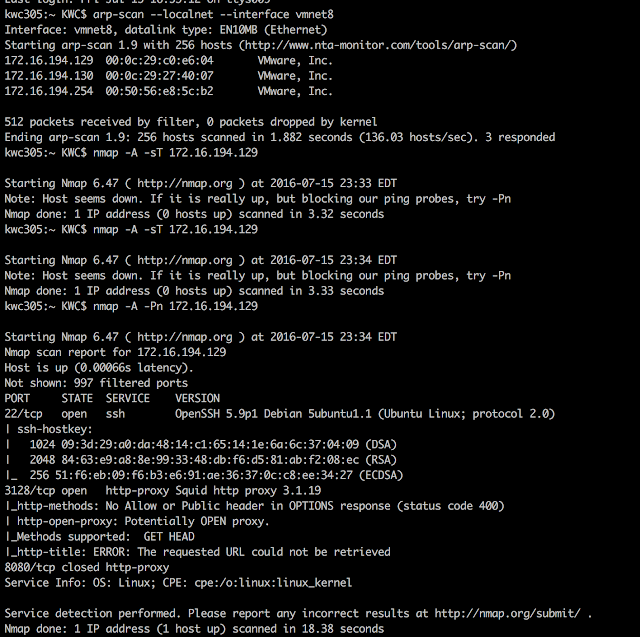
Vulnhub Stapler1.0 Writeup All information can be found on www.vulnhub.com ---------summary------- 1. information gathering 2. host exploitation by reverse shell 3. escalate privilege ---------start--------- After boot up the download VM, the system's login page Since we don't know the IP address, we use arp-scan to get IP. Here IP is 172.16.194.138(under NAT protocol) After know the IP, next step is use NMAP to see if there's any information, here we see port 80, 666, 3306 and 12380 are interesting. First I tried port 80, but no other information I can get, so I tried https with port 12380 here is the port 12380, it seems have more information As usual, try to see if /robots.txt is exist, and luckily it is. It comes with 2 website here. First is /admin112233, but only have pop-up screen and redirect to another page. Next, I tried /blogblog and I got really interesting stuff here, is a blog. From here, I can