Vulnhub SickOs1
# CTF-WriteupSickOs1
all resource can be found on www.vulnhub.comUse arp-scan to get target's IP
And NMAP to scan the target
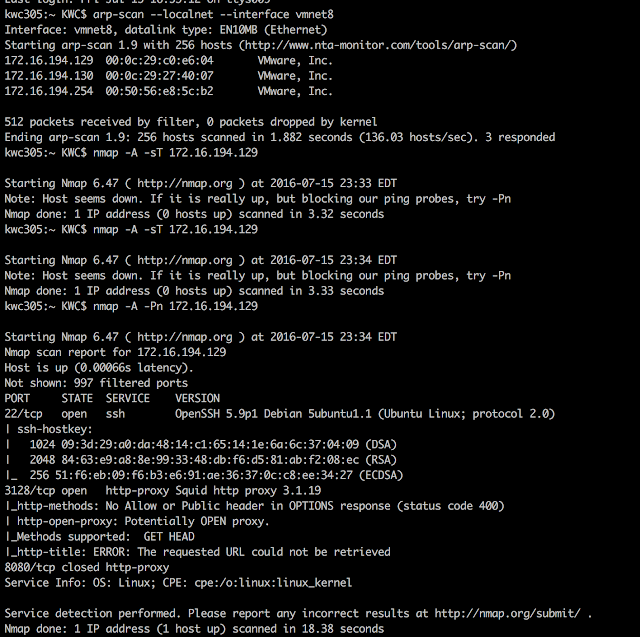
We found port 3128 is open, next step use nikto to scan if there's any vulnerability.
We found a shellshock, which can be use on attack. Also we found a /robots.txt file
Next, port 3128 is a proxy server, so I use firefox to set proxy on port 3128 and go to localhost. I got this picture:
Based on the nikto, we can enter localhost/robots.txt, and got /wolfcms
So, I decided go to this /wolfcms page and see a website
For wolf CMS, it's admin page URL is /?/admin, and a good start username/password is admin/admin
Go through the login page, next step is found is there any place we can upload a reverse shell to connect back to my host. And is on files folder, I can upload files
This time, I use php-reverse-shell.php as my upload file
upload to 3128 server, also need to chmod 777
open netcat, and use browser to see the payload file, let nc connect remotely
escalate your privilege by python :
python -c 'import pty; pty.spawn("/bin/bash")'
now we still need to escalate to root
there is a config file in /var/www/wolf include username and password
We can use this usr/pwd as way to have higher privilege, final step is sudo su
Finally, I have the highest privilege.
Basically, always starts from nmap and nikto, which can provide many information and vulnerability.
Next is try to find is there any place can put your payload or backdoor.
Finally is using netcat or metasploit to exploit and escalate privilege .













感謝您的分享 受益良多 ~^^~ 希望看完你的部落格後可以變成駭客大師
回覆刪除我先變神奇寶貝大師啦!!!!
回覆刪除