Vulnhub: BNE0x03 - Simple
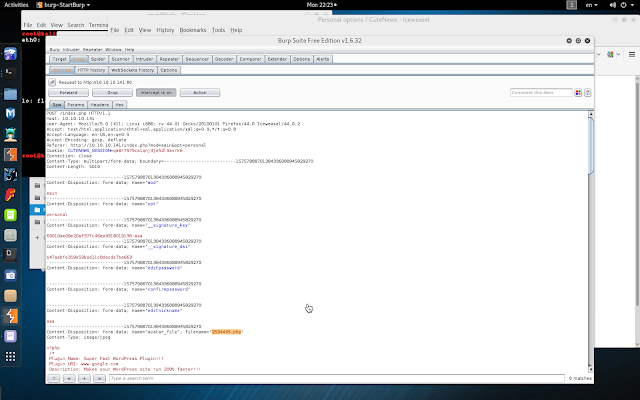
Vulnhub: BNE0x03 - Simple VM can be downloaded here: https://www.vulnhub.com/entry/sectalks-bne0x03-simple,141/ Sum: As hint on vulnhub, normally reverse shell and Privilege Escalation on exploit-db 1. Identify target: (vmnet3 is base on which subnet machine is locate, could be eth0 or others) $ arp-scan --interface=vmnet3 --localnet Interface: vmnet3, datalink type: EN10MB (Ethernet) Starting arp-scan 1.9 with 256 hosts (http://www.nta-monitor.com/tools/arp-scan/) 10.10.10.140 00:0c:29:53:94:f3 VMware, Inc. 10.10.10.141 00:0c:29:53:94:f3 VMware, Inc. 10.10.10.142 00:0c:29:8e:0e:32 VMware, Inc. 10.10.10.254 00:50:56:f5:e7:d2 VMware, Inc. 513 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.9: 256 hosts scanned in 1.849 seconds (138.45 hosts/sec). 4 responded 140, 141 is target IP, 142 is attacker(Kali) 2. Nmap scan: root@kali:~/Desktop# nmap -A 10.10.10.140 Starting Nmap 7.01 ( https://nmap.org ) at 2017-09-25 13:12